Aug 20, 2024
The Intersection of Compliance and Risk vs Security in Financial Services
FSIs face rising compliance demands, squeezing budgets and cybersecurity risks. Open-source tech and careful vendor selection can mitigate these challenges.
Michael Coates
|RSS FeedSenior Solution Architect
As explored in our two most recent blogs, changing compliance regulations and policies by specific regions and countries are having a significant impact on financial services institutions (FSIs). This regulatory change puts a further squeeze on FSI budgets, with operational resilience rules already in effect in the UK and commencing in Australia in 2025 with CPS 230/234. Maintaining operational security and reducing the impact of risk events continues to be brought to the forefront of the finance industry in recent months.
The recent Deloitte Report, 2023 Cybersecurity for financial services survey, highlights this focus, finding cybersecurity budgets are more constrained when compared to previous years. After digital transformation, regulatory pressure is the most important business driver, and cybersecurity functions are increasingly focusing on business impact and risk, not just technology challenges.
Noting the intersection of security and regulatory risk reduction, the report states, “Regulatory drivers account for more than half of the cybersecurity budget at 46% of the firms surveyed in 2023, not far short of the 54% who report that strategic priorities are dominant.”
In this blog, we’ll take a closer look at how compliance, risk, and security intersect through the ICT lens, including the important consideration of how to best secure data within an organization .
Don’t underestimate the impact of vendor choice
There are teams within an average FSI organization that are completely dedicated to managing risk, however, within the ICT team there is a different perspective on risk. This perspective includes guaranteeing uptime, availability, security of data, contractual stability, and management of costs. It’s about ensuring there are ample resources available and they’re well managed.
An important part of mitigating risk for any FSI is to carefully review supplier contracts. Keep in mind that third party vendors can still introduce risk to your organization regardless of the contract imposed or what the vendor promises.
In some cases, clients will try to lessen the number of vendors they engage with to avoid acting as a system integrator. However, going all-in on one vendor presents its own risks/challenges, particularly when thinking about your cloud vendor requirements. For instance, a region may go offline, or you may lose your pricing leverage and the ability to make a deal, and even in the midst of overspending the cost to move can outweigh the benefit of doing so.
To avoid being locked into a single provider, FSIs must choose technologies that are easy to resource and vendor agnostic, like open source solutions. By using open source technologies, organizations can:
- Take advantage of widely-adopted technologies that are commonplace, well understood, and supported by broad communities
- Eliminate the reliance on proprietary software from a single vendor
- Reduce the need for high cost vendor-specific skills
The role and rationale for security mandates
While the compliance and risk team sets policies, it's up to the security team to implement them. For example, a policy sets data encryption requirements and the security team must ensure that data is encrypted both at rest and in motion. Another policy may define who can access certain datasets, and the security team must implement detailed and granular access control lists and be able to perform detailed audits to prove compliance with the policy. Another example is Personal Private Information (PPI) compliance, where security teams must be able to mask or anonymize PPI information and demonstrate compliance with data privacy mandates.
With new regulations around data sovereignty and transfer between regions, having control over where your data lives is perennially important. Data sovereignty refers to the right of a group or individual to control the collection, storage, and interpretation of their data, subject to the laws of where that data is collected. This includes data such as personal information, intellectual property, or financial data. FSIs must comply with data sovereignty regulations both when data is collected and stored, and when transferred between regions for high availability or disaster recovery purposes.
To create relevant mandates and policies, security teams must first know where data lives. Is it running in the customer’s private cloud environment or the service provider's environment? How much control does the business have over the data? Can the business lock the service provider out of it if needed?
At Aiven, we offer various options to ensure the objectives across security, technology, and risk teams are met. For instance, the Bring Your Own Cloud (BYOC) deployment option ensures the business can run a service within their cloud account and retain total control, limiting access to data and actions that Aiven can take. More specifically, Aiven can continue to monitor the services running, backups, and more within the customer’s cloud account, but the customer can restrict Aiven’s access to sensitive data or systems by clicking ‘remove access entirely’ if they deem it necessary.
Saving on money and risk with the right partner
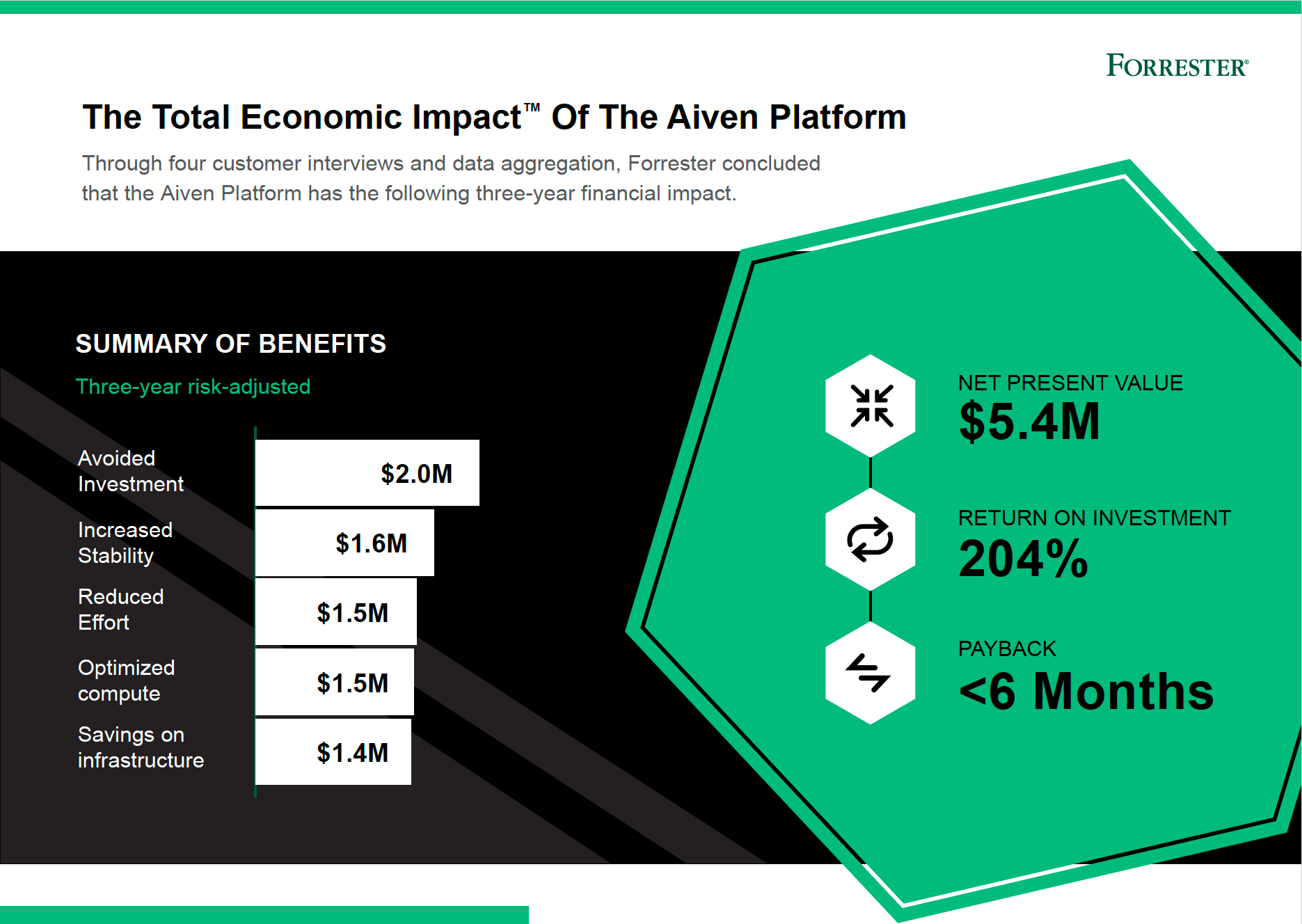
As highlighted in Forrester’s The Total Economic Impact of the Aiven Platform, choosing the right managed services partner can help FSIs save significantly on reducing risk events and supporting teams.
As the report says, “Severe adverse events are uncommon, but nonetheless occur. The composite organization experiences an average impact value of $300,000 and four adverse events in Year 1, two in Year 2, and one in Year 3.” Because of this, the present value savings of increased reliability and resilience over three years amounts to $1.6 million. Adding up the total quantifiable risk-adjusted present value (PV) benefits for the composite organization over three years amounts to $5.4 million with a payback period of less than six months.
Aiven takes a security-first approach. We provide dedicated virtual machines instead of multi-tenant virtual machines, automated security updates, and annual security testing. All data is fully encrypted end-to-end at rest and in transit, including support for Dedicated VPC Peering on Aiven Cloud to provide fine grained network access control. These features help certify Aiven’s compliance with global standards, including ISAE 3000, ISO27K, GDPR, CCPA, HIPAA and PCI DSS.
Our customers choose Aiven because we:
- Simplify data infrastructure across one or multiple clouds through a unified platform
- Offer widely-adopted open source technologies to reduce reliance on proprietary solutions and high cost vendor-specific skills
- Provide automatic software updates with zero downtime to ensure software remains up-to-date and compliant
- Backup data to three availability zones for high availability and disaster recovery
- Secure data end-to-end, at rest and in motion
- Provide 24/7/365 support anywhere in the world
To see how you can improve your security and risk management while also maximizing your tech spend, contact Aiven.
Stay updated with Aiven
Subscribe for the latest news and insights on open source, Aiven offerings, and more.